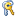| Dialog box element | Description | ||||
|---|---|---|---|---|---|
Type of VPN |
Lists the available remote access server types you can call. Choices vary, depending on the type of connection. If a host name or Internet Protocol version 4 (IPv4) address is entered in the General tab, the type of VPN allowed is: Automatic, PPTP, or L2TP/IPsec. If an Internet Protocol version 6 (IPv6) address is entered in the General tab, the type of VPN allowed is: Automatic or L2TP/IPsec. If you are not sure which type to select, click Automatic. Point-to-Point Tunneling Protocol (PPTP) is attempted first, and then Layer Two Tunneling Protocl (L2TP). If you know the type of VPN server to which you are trying to connect, then select the appropriate server type. In order to connect to an L2TP server, the Trusted Root Certification Authorities certificate store on your computer must contain the certificate of the root authority for the certification authority (CA) that issued your computer certificate and the certificate for the L2TP server. If you select Automatic or Layer 2 Tunneling Protocol with IPsec (L2TP/IPsec), then you can specify the IPsec authentication settings by clicking Advanced Settings. |
||||
Data encryption |
Specifies whether the connection requires the use of data encryption. You can specify that encryption is not used, that encryption is optional, that encryption is required, or that maximum strength encryption is required. |
||||
Authentication |
Specifies the authentication methods that are used to establish the VPN. You can select one of the following options:
|