In most Domain Name System (DNS) lookups, clients typically perform a forward lookup, which is a search that is based on the DNS name of another computer as it is stored in a host (A) resource record. This type of query expects an IP address as the resource data for the answered response.
DNS also provides a reverse lookup process, in which clients use a known IP address and look up a computer name based on its address. A reverse lookup takes the form of a question, such as "Can you tell me the DNS name of the computer that uses the IP address 192.168.1.20?"
DNS was not originally designed to support this type of query. One problem in supporting the reverse query process is the difference in how the DNS namespace organizes and indexes names and how IP addresses are assigned. If the only method to answer the previous question is to search in all domains in the DNS namespace, a reverse query would take too long and require too much processing to be useful.
To solve this problem, a special domain, the in-addr.arpa domain, was defined in the DNS standards and reserved in the Internet DNS namespace to provide a practical and reliable way to perform reverse queries. To create the reverse namespace, subdomains within the in-addr.arpa domain are formed, using the reverse ordering of the numbers in the dotted-decimal notation of IP addresses.
This reversed ordering of the domains for each octet value is necessary because, unlike DNS names, when IP addresses are read from left to right, they are interpreted in the opposite manner. When an IP address is read from left to right, it is viewed from its most generalized information (an IP network address) in the first part of the address to the more specific information (an IP host address) that is contained in the last octets.
For this reason, the order of IP address octets must be reversed when the in-addr.arpa domain tree is built. The IP addresses of the DNS in-addr.arpa tree can be delegated to organizations as they are assigned a specific or limited set of IP addresses within the Internet-defined address classes.
Finally, the in-addr.arpa domain tree, as it is built into DNS, requires an additional resource record type—the pointer (PTR) resource record—to be defined. This resource record creates a mapping in the reverse lookup zone that typically corresponds to a named host (A) resource record for the DNS computer name of a host in its forward lookup zone.
The in-addr.arpa domain applies to all TCP/IP networks that are based on Internet Protocol version 4 (IPv4) addressing. The New Zone Wizard automatically assumes that you are using this domain when you create a new reverse lookup zone.
If you are installing DNS and configuring reverse lookup zones for an Internet Protocol version 6 (IPv6) network, you can specify an exact name in the New Zone Wizard. This way, you can create reverse lookup zones in DNS Manager that can support IPv6 networks, which use a different special domain name, the ip6.arpa domain.
Additional information is available about IPv6 and DNS, including examples of how to create and use ip6.arpa domain names, in Request for Comments (RFC) 3596, "DNS Extensions to support IP version 6." For more information, refer directly to this RFC, which you can find on the RFC Editor Web site (
Example: reverse query (for IPv4 networks)
The following illustration shows an example of a reverse query that is initiated by a DNS client to learn the name of another host (host-a) based on its IP address: 192.168.1.20.
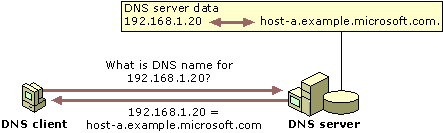
The reverse query process follows these steps:
-
The client queries the DNS server for a pointer (PTR) resource record that maps to the IP address of 192.168.1.20 for host-a.
Because the query is for pointer (PTR) resource records, the resolver reverses the address and appends the in-addr.arpa domain to the end of the reverse address. This forms the fully qualified domain name (FQDN) (20.1.168.192.in-addr.arpa.) to be searched in a reverse lookup zone.
-
After it is located, the authoritative DNS server for 20.1.168.192.in-addr.arpa can respond with the pointer (PTR) resource record information. This includes the DNS domain name for host-a, which completes the reverse lookup process.
Remember that, if the queried reverse name is not answerable from the DNS server, normal DNS resolution (either recursion or iteration) can be used to locate a DNS server that is authoritative for the reverse lookup zone and that contains the queried name. In this sense, the name resolution process that is used in a reverse lookup is identical to that of a forward lookup.
Inverse queries
Use of inverse queries is an outdated practice, originally proposed as part of the DNS standard to look up a host name based on its IP address. They use a nonstandard DNS query operation, and their use is limited to some of the earlier versions of Nslookup, a command-line utility for troubleshooting and testing the DNS Server service.
The DNS Server service recognizes and accepts inverse query messages, answering them with a fake inverse query response. For DNS servers running in Windows NT® Server 4.0, this support is available by default if the server computer has been updated to Service Pack 4 (SP4) or later.
 | Note |
|
The configuration of pointer (PTR) resource records and reverse lookup zones for identifying hosts by reverse query is strictly an optional part of the DNS standard implementation. You are not required to use reverse lookup zones, although for some networked applications, they are used to perform security checks. |